Exploit Development
On these pages we'll explore the fascinating topic of developing exploits. We'll compromise the security of software to make it do things it was never intended to do. Never will we modify the program under attack, however. All of the tricks and techniques we apply here will be done through typical and not-so-typical user input. By learning about vulnerabilities and how to take of advantage of them, you can write more code and also develop in-depth understanding of how computers work at the lowest levels.
Stack Corruption for Newbies
This is an introductory tutorial that walks the reader through attacking a very simple and vulnerable program. It serves as a base from which
other techniques can be learned and introduces a fundamental technique: the buffer overflow. I wrote it to be accessible to pretty much
everyone. Even if you don't write code or play with bits and bytes, check this one out. It gives a glimpse into how hackers break code and make
programs behave in unexpected ways.

EIP Redirection
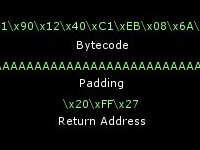
Here we'll explore how a hacker can make a vulnerable program jump to any part of code that he wants. We'll use a buffer overflow technique to
overwrite a return address and direct the program flow. The target in this case is a normally unreachable function. The tools, concepts, and
techniques explained here are vital building blocks to writing full-on exploits. Enjoy!
Executing Arbitrary Code
This one moves along at a slightly faster pace but ensures that the concept is explained thoroughly. We'll the EIP redirection technique in the
last tutorial to make the program jump into code that we feed it. We'll even use the very same overflowed buffer to store our "malicious" code.
Check it out and let me know what you think.
SFP Overwrite
I thought you guys might find this one interesting; I haven't seen it before. Instead of overwriting the return address on a function vulnerable
to a buffer overflow, we can go after its Saved Frame Pointer. This essentially allows us to hijack the calling function's perception of the stack.
There are likely much more powerful uses for this trick but I present this example to explain the concept. If you guys know of any other uses for
this sort of thing, I'd love to hear them.
Format String Bugs
In this one, we'll check out a very different sort of vulnerability and leverage it to read a critical value off the stack. This tutorial is really
only an introduction to this cool class of attacks. Format string bugs don't rely on overflowed buffers; everything stays where its supposed to in
memory. So what was the programmer's security sin this time? He said "hello" to the user the wrong way...